Types of Hackers
Introduction
In the ever-evolving landscape of cyberspace, the term “hacker” carries diverse connotations. While some hackers contribute to the greater good by fortifying digital defenses, others exploit vulnerabilities for malicious purposes. This article embarks on a journey to unravel the various types of hackers, shedding light on their motivations, methodologies, and the impact they have on the world of cyber security.
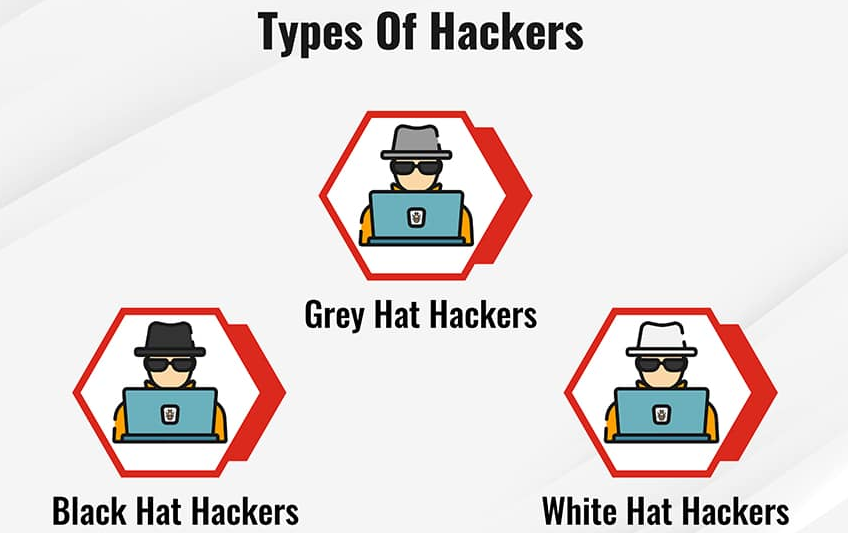
Types of Hackers
The White Hats: Ethical Hackers
White Hat Hackers – Guardians of Cyber Security
White hat hackers, often referred to as ethical hackers, don the mantle of cyber security defenders. These individuals deploy their skills to identify vulnerabilities and strengthen digital fortresses. Ethical hacking is a crucial aspect of cyber security, involving penetration testing, vulnerability assessments, and proactive defense strategies.
Resource: Certified Ethical Hacker (CEH) Certification
The Gray Area: Gray Hat Hackers
Gray Hat Hackers – Navigating the Moral Ambiguity
Gray hat hackers occupy the nebulous space between ethical and malicious hacking. While they may uncover vulnerabilities without malicious intent, they often do so without proper authorization. Gray hat hackers may notify the affected parties after discovery, but their actions blur the ethical boundaries of hacking.
Resource: The Ethics of Hacking: Gray Hat Hackers
The Dark Side: Black Hat Hackers
Black Hat Hackers – Agents of Cyber Mischief
In the realm of cyber security, black hat hackers epitomize the dark side. Motivated by malicious intent, they exploit vulnerabilities for personal gain, financial theft, or cyber vandalism. Cyber criminals often fall into this category, launching attacks ranging from data breaches to ransomware campaigns.
Resource: Understanding Black Hat Hackers
The Shadows: Hacktivists
Hacktivists – Merging Technology and Activism
Hacktivists are driven by a cause, using hacking as a tool for political or social activism. While their motives may align with a perceived greater good, hacktivist actions can lead to significant disruptions, defacements, or data breaches. Notable hacktivist groups include Anonymous and Lizard Squad.
Resource: Hacktivism: A Short History of Hacktivist Groups
The Disruptors: Script Kiddies
Script Kiddies – Novices in the World of Hacking
Script kiddies are individuals with limited technical skills who use readily available hacking tools and scripts. While they lack the expertise of seasoned hackers, their actions can still cause disruptions. Script kiddies often engage in cyber mischief without a clear agenda, seeking notoriety or simply enjoying the thrill of unauthorized access.
Resource: The Rise of Script Kiddies and the Underground Hacking Scene
The Inside Job: Insiders
Insiders – Threats from Within
Insiders pose a unique threat as they operate from within an organization. These individuals, whether employees or contractors, exploit their privileged access for personal gain or to enact revenge. Insider threats can result in data leaks, intellectual property theft, or sabotage.
Resource: Insider Threats: A Comprehensive Guide
Hacking Techniques and Methodologies
1. Phishing Attacks
Phishing attacks involve tricking individuals into divulging sensitive information, often through deceptive emails or websites. Hackers, especially those engaged in social engineering, leverage psychological tactics to manipulate targets.
Resource: How to Recognize and Avoid Phishing Scams
2. Malware Deployment
Malicious software, or malware, encompasses a range of threats such as viruses, worms, and ransomware. Hackers deploy malware to compromise systems, steal data, or disrupt operations.
Resource: Types of Malware and How to Defend Against Them
3. Denial of Service (DoS) Attacks
DoS attacks aim to overwhelm a system, network, or website with traffic, rendering it inaccessible to users. Distributed Denial of Service (DDoS) attacks involve a network of compromised devices working in concert to amplify the impact.
Resource: How to Protect Against DDoS Attacks
4. SQL Injection
SQL injection involves exploiting vulnerabilities in web applications by injecting malicious SQL code. This technique allows hackers to manipulate databases, potentially gaining unauthorized access to sensitive information.
Resource: Understanding SQL Injection Attacks
5. Man-in-the-Middle (MitM) Attacks
MitM attacks involve intercepting and potentially altering communication between two parties without their knowledge. This can lead to the theft of sensitive data, including login credentials and financial information.
Resource: Man-in-the-Middle Attacks Explained
Safeguarding Against Hacker Threats
1. Education and Training
Ensuring that individuals, from end-users to IT professionals, are educated about cyber threats and best practices is paramount. Training programs and awareness initiatives help build a proactive defense against hacking attempts.
Resource: Cyber Security Awareness Training Programs
2. Advanced Security Measures
Implementing robust security measures, including firewalls, intrusion detection systems, and encryption, forms a crucial line of defense. Regular updates and patches mitigate vulnerabilities that hackers might exploit.
Resource: Best Practices for Cyber Security
3. Incident Response Plans
Having a well-defined incident response plan is crucial for minimizing the impact of a cyber attack. Timely detection, containment, and recovery strategies are essential components of an effective response.
Resource: Incident Response Planning Guide
4. Zero Trust Security Model
The Zero Trust security model challenges the traditional approach by assuming that threats can exist both outside and inside the network. Verification of identities and strict access controls are implemented at every level, reducing the risk of unauthorized access.
Resource: Zero Trust Architecture Guide

Conclusion
In the intricate dance between hackers and defenders, the world of cyber security remains dynamic and ever-changing. Understanding the types of hackers, their motivations, and the techniques they employ is a crucial step toward fortifying our digital fortresses.
As we navigate the cyber frontier, the imperative to stay vigilant, educated, and proactive becomes clear. By embracing ethical hacking practices, fortifying security measures, and fostering a culture of cyber resilience, we can collectively mitigate the risks posed by malicious hackers.
In conclusion, the world of cyber security is a battlefield where knowledge, innovation, and preparedness serve as our greatest weapons. As technology advances, so too must our defenses evolve. By staying informed, investing in robust security practices, and fostering a collaborative approach to cyber security, we can navigate the digital landscape with confidence and resilience. In the grand tapestry of cyberspace, each defender plays a vital role in ensuring a secure and interconnected future.
Also read this(recommended)




